As an interesting research project, Pan Vagenas, one of our researchers, took a closer look at abandoned plugins in the WordPress repository. His work was inspired by a recent post by Isabel Castillo where she lists the oldest abandoned plugins in the WordPress plugin repository.
An abandoned plugin is one that has not been updated for several years. According to Isabel’s post there are several plugins that have a large install base that haven’t been updated for some time:
“Exec-PHP plugin by Sören Weber has over 100,000 active installs despite that it has not been updated since June of 2009. Category Order by Wessley Roche has over 90,000 active installs even though it was last updated in May of 2008. Ultimate Google Analytics by Wilfred van der Deijl has over 80,000 installs even though it was last updated more than nine years ago.”
We took a look at the plugin repository and discovered the following:
- There are currently a total of 37,300 plugins available in theWordPress.org repository
- 17,383 of those plugins have not been updated in the past 2 years.
- 13,655 plugins have a compatibility tag of 3.x. WordPress 4.0 was released in September 2014.
- 3,990 plugins have not been updated since 2010 which is over 7 years ago.
- There are 29,892 additional WordPress plugins in the plugin source code repository that are not listed in WordPress.org in the plugin directory.
Unmaintained Plugins with Vulnerabilities
During our analysis, we found 18 abandoned plugins that are currently available for installation from the WordPress plugin repository that appear to have vulnerabilities that have not been fixed. In each case the plugin has not been updated for 2 years or more. Some of them have thousands of active installs.
We also found 4 plugins (marked with asterisks in the table below) that have fixed a vulnerability, but their fix was released in such a way that existing users are not updated to the newest fixed version. In each case, the author committed a fix to trunk but did not increment the version number and tag it properly in the plugin repository, so their users remain vulnerable.
The following table lists the plugins that we found, along with number of active installs and the details about each vulnerability. Several plugins are listed multiple times because they have had multiple vulnerabilities reported.
Note that all vulnerabilities published here have been publicly known for 2 to 3 years. These are all old vulnerabilities which have been publicly disclosed and have not been fixed by the plugin author. Please see our suggestions after the table on what to do if you are the plugin author or if you are a plugin user.
What to do if you use one of the plugins above
If the plugin is not marked with an asterisk, we suggest you disable the plugin and remove it from your system. Then immediately contact the plugin author and ask for clarification on whether the plugin has a vulnerability or not. You can direct the author to this blog post which includes suggested actions for plugin authors below. You should start with the plugin support forum on wordpress.org for a particular plugin.
If the plugin is marked with an asterisk, you can disable and remove the plugin. Then reinstall it and you should have a newer version. We have not audited individual plugins for security so we can not verify whether a vulnerability has been comprehensively fixed.
What to do if you are the author of a plugin mentioned above
If you are the author of one of these plugins and have not fixed one of the reported vulnerabilities, we recommend you do so immediately and release a fix to your customers. Then follow the steps in the bullet list below.
If your plugin is marked with an asterisk, we suggest you read the section on the WordPress codex on updating your plugin. Create a new version for your plugin so that existing users will be updated to the fixed version, tag the release and follow the additional steps we suggest below.
If you have fixed a vulnerability in your plugin and we included it above, then you did not mention it in your changelog and it has not been recorded on the wpvulndb website, the source of our data above.
We suggest you take the following actions:
- Update your changelog and mention that you fixed a vulnerability and what the vulnerability was that was fixed.
- Contact the wpvulndb project and ask them to update their database to indicate that your plugin has been fixed. Right now their database shows no entry for a version that your vulnerability was fixed in.
- You should also consider visiting the source of wpvulndb’s data which is often a security mailing list. On that list you’ll find the researcher who discovered your vulnerability. You should drop them a note letting them know the vulnerability has been fixed.
Evaluating Plugins
If you are a WordPress site owner, it is important that you evaluate each plugin carefully before you install it. Check how long it has been since the last update. If it has been more than 2 years, you should think twice before installing the plugin because it is no longer actively maintained. You may consider reaching out to the author or posting on the support forum to find out more information.
The plugin repository is one of WordPress’s greatest assets because it provides a huge amount of code and a large number of applications that extend WordPress. It is also completely open and anyone can contribute. There is no formal source code auditing process or security analysis done on a plugin when it is submitted. There is also no ongoing auditing process for each subsequent release.
A large number of plugin updates are submitted to the WordPress repository every day. For this reason it is important that you gain at least a basic understanding of who is behind a particular plugin before you install it. Here are a few steps you can take to evaluate whether you should use a plugin:
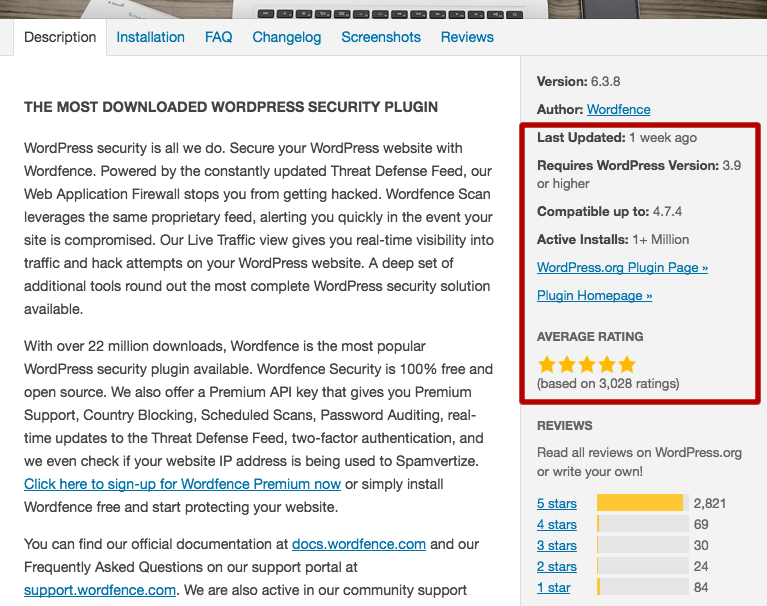
- Check the average plugin rating.
- Check when it was last updated.
- Check that it is compatible with the current version of WordPress.
- Check the number of active installs the plugin has. Some reliable and useful plugins have low install numbers but you should examine a plugin carefully if it has a low install base (below 1,000 active installs). It may not be maintained.
You can find all this information when you add the plugin in WordPress. Simply click on the plugin title and you’ll find the following. We have highlighted the section you should pay attention to below:
Conclusion
Plugins can make adding functionality to your website incredibly easy and are a big part of why WordPress is such a popular platform. The plugin repository on WordPress.org is an incredible resource, but as we have shown above it contains both abandoned plugins and ones with known vulnerabilities. Every plugin you add to your site increases your security risk, and you should evaluate each one to make sure it is being properly maintained.
As always we welcome your comments below. Special thanks to our security researcher Pan Vagenas who compiled the research we included in this post.
The post 22 Abandoned WordPress Plugins with Vulnerabilities appeared first on Wordfence.