Yesterday at 7pm UTC (noon PDT) we saw the volume of brute force attacks on the WordPress sites that we protect more than double from the average for the previous 24 hours. The number of attacking IPs more than tripled.
The chart below shows the count of attacks per hour from June 12th onward. You can see a very obvious spike followed by about a 10-hour pull-back, and then another surge almost back to the high we saw with the spike.

We dug into the IP addresses behind the attacks to try to figure out who or what is behind the abrupt surge.
Home Routers Again?
Back in April, we wrote about a home router botnet that was being used to attack WordPress websites. Many of those attacks were originating from IPs that had a specific port (7547) open and were running a vulnerable version of remote management software called Rompager. We published a list of 28 ISPs with suspicious attack patterns indicating compromised routers and built a tool that checks if your router is vulnerable. In early May we wrote about that same botnet shutting down.
In the table below we show the top 20 ISPs by number of IP addresses involved in the latest surge and actively attacking. We also show the average number of hourly attacks per IP. Please note the the average is likely understated, as we accumulated attacks during a four-hour window and did not account for IPs that started or stopped attacking in the middle of the time window.
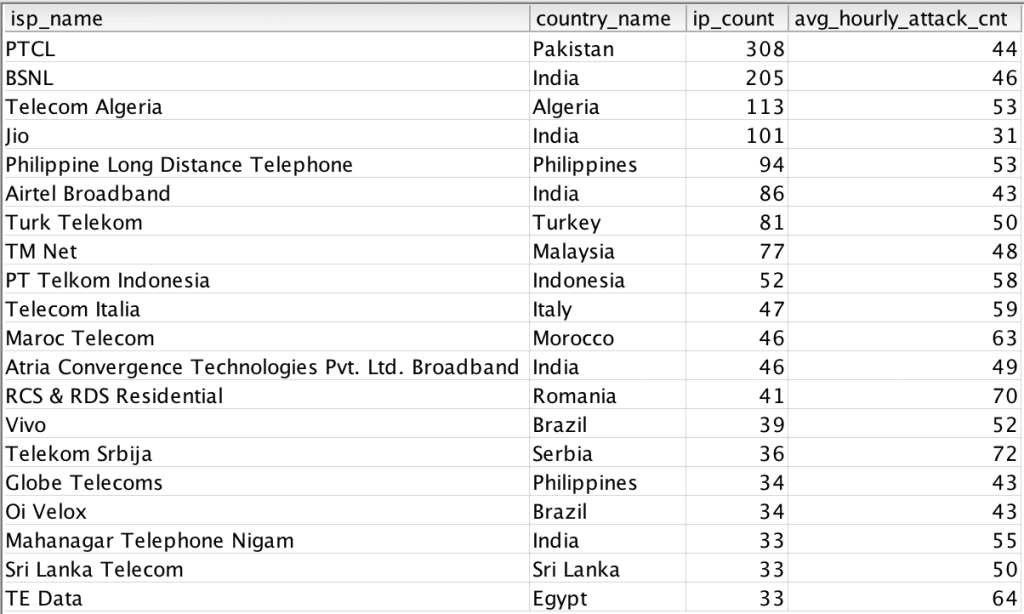
Comparing that list to the ISPs with the most new attacking IPs yields interesting results. Of the top 20 ISPs involved in attack surge, all 20 of them were on our earlier list of 28. The IPs are also attacking at low volume, which is consistent with what we saw in April. We also spot checked many of the IPs, and did find port 7547 open on some of them.
While we cannot be 100% certain that the surge in attack volume can be attributed to the home router botnet we wrote about in April or the attacker that was behind it, the data very strongly suggests it is. We will continue to monitor the attacks and report on anything interesting we find here on the blog.
How Does This Impact You?
Most site owners should expect to see a significant increase in password-guessing attack volume, if they haven’t already. We have written at length about how to protect against brute force attacks, including the serendipitous Learning Center article that we posted yesterday, Introduction to Brute Force Attacks. In that article, we mention several steps you can immediately take on your websites to harden your defenses against brute force password-guessing attacks as much as possible, which will make your website really, really tough to break into. The harder it is to guess your username and password and break through your site’s defenses, the greater the likelihood that any would-be hacker will simply move on to a much easier target.
The Wordfence Premium IP Blacklist responded to the attacks beautifully, growing from 1,444 IPs before the attack to 5,592 three hours later. At the time of this writing there are 6,928 IPs on the list and it continues to grow. At the height of the previous botnet attack there were over 10,000 IPs on the blacklist.
For those of you who aren’t certain that your site security is up to the challenge, you might consider having our security services team audit your site security. It costs $149 and includes a one-year Wordfence Premium subscription.
The post Home Router Botnet Resumes Attacks appeared first on Wordfence.
