In a rather unfortunate turn of events earlier this month, the Hollywood Presbyterian Medical Center was infected with ransomware. Ransomware, if you’re unfamiliar with it, encrypts everything on your workstation and then tells you to pay an attacker to decrypt your system and regain access to your information.
In the case of Presbyterian, they had to pay 40 bitcoins or the equivalent of $17,000 to regain access to their systems. The ransomware attack affected CT scans, documentation, lab work, pharmacy functions and their email went down. Last week they paid the attacker the $17,000 and their systems were decrypted and they’re back online.
Unfortunately WordPress has been a source of ransomware infections. It’s unknown whether it contributed to the Presbyterian attack or not. During the past month the information security industry has seen WordPress used as a kind of platform to launch ransomware attacks. It works as follows:
- A WordPress site is hacked through any method available. That may be a brute force password guessing attack or by exploiting a vulnerability in a plugin, theme or core.
- The attacker installs code on the WordPress site that redirects visitors to other infected websites that are running the Nuclear Exploit Kit. The redirects may happen through a series of websites to try and prevent web browsers and Google from warning you that a site is infected. The sites involved in the redirect change frequently.
- When a visitor to the infected site is redirected, the nuclear exploit kit searches for vulnerabilities in the site visitor’s Flash Plugin, Microsoft Silverlight, Adobe Reader or Internet Explorer.
- If Nuclear finds a vulnerability, it exploits the visitor machine and installs the TeslaCrypt Ransomware.
- The ransomware then encrypts all files on the workstation and extorts the owner into paying to get their system decrypted.
This is what TeslaCrypt looks like:
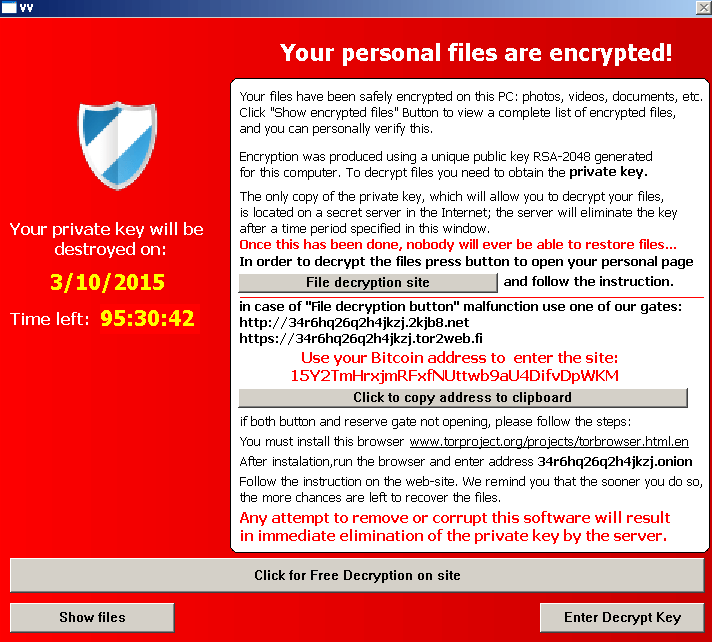
A screenshot of the screen that TeslaCrypt displays when your files are encrypted. Courtesy Bromium Labs.
As you can tell from the sequence of events above, TeslaCrypt and the attackers behind it rely on a cascade of failures. They require multiple vulnerable WordPress sites to perform their infection and to set up a chain of redirects. They then need a visitor using an unpatched workstation with vulnerable applications to visit an infected site.
The fact that Hollywood Presbyterian actually paid the ransom to regain access to their systems, speaks volumes about how effective a ransomware attack is and the impact it has on systems.
Update: If you are infected with TeslaCrypt, there is a utility available written by an anonymous researcher called TeslaCrack which may help. Thanks to Samuel who posted it in the comments below, where you can find a link to the utility along with a few other links I’ve added discussing the utility.
In another turn of events, the Linux distribution “Mint” reported on Saturday that they had their website hacked via a WordPress installation. According to Clement Lefebvre, the project leader, in reply to a comment on their blog:
“We found an uploaded php backdoor in the theme directory of a wordpress installation, which was 1 day old and had no plugins running. The theme was new but most importantly I think we had lax file permissions on this. This was only set up hours before the attack but we were probably scanned for something like this for a while. Anyhow, we don’t know yet how it was uploaded but we know it happened there, and I’m certainly not pointing the finger at anybody. People just asked if we were running wordpress or if wordpress was used in the attack and I answered yes.”
The attacker replaced the real Linux distribution that Mint users download from the site with a version that had malware installed. The modified Linux distribution turns your Linux machine into a member of an attack botnet that can be used for DDoS attacks.
As WordPress site owners, our role in this is clear. If you don’t protect your WordPress site from attackers, you risk infecting your site visitors with Ransomware, turning their machines into an attack platform, or worse.
When thinking about WordPress security, it’s important to consider the broader impact a hack might have, and the larger responsibility that we as site admins have to not just protect our own website and our investment, but our site members’ personally identifiable data and the security of visitors to our websites.
At Wordfence, we continue to provide detailed advice on how to keep your WordPress site secure including here on our blog and in our WordPress Security Learning Center. Securing your site is critically important, not just to protect your investment, but for your site visitors’ safety.
In other news: We’d like to remind all ElegantThemes customers to update their themes if they haven’t already. There was a critical security update released on Thursday that fixed a vulnerability in several of their themes. Update immediately if you haven’t done so already.
As always we welcome your comments below. Please share this with the larger community to create awareness of our larger responsibility as WordPress site administrators.
The post WordPress-Delivered Ransomware and Hacked Linux Distributions appeared first on Wordfence.
